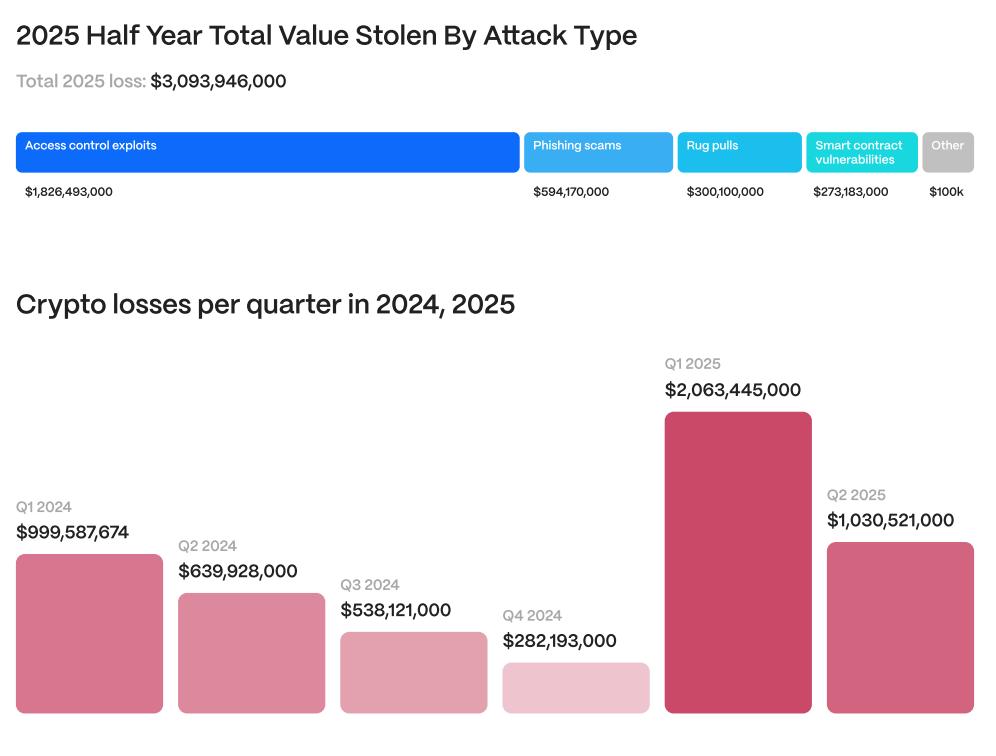
In the first half of 2025, the crypto asset industry lost over $3.1 billion due to cyber attacks, with access control vulnerabilities being the main cause.
Only in the first half of 2025, the crypto asset industry recorded severe losses of over $3.1 billion due to cyber attacks, far exceeding the total loss of $2.85 billion in 2024. According to the latest report from blockchain security audit company Hacken, most of these incidents originated from fundamental vulnerabilities in access control mechanisms.
Notably, the attack on Bybit exchange in February, with losses of $1.5 billion, was an especially serious case but also highlighted the general trend that the entire industry is facing systemic security challenges.
Source: Hacken's Web3 Security Report for the First Half of 2025
Hacken's analysis clearly shows that exploiting access control vulnerabilities accounts for 59% of total losses, reflecting a change in hackers' strategy. Instead of focusing only on encryption errors in smart contracts - which caused only about 8% of losses ($263 million) - hackers are increasingly targeting vulnerabilities in operational processes and human factors.
Attack techniques such as blind signing, personal key leaks, and sophisticated fraud campaigns are becoming increasingly common, making access control a neglected weak point. Mr. Yehor Rudytsia, Hacken's Head of Investigations, warns that projects need to pay special attention to old or inherited source code, as these are often systems that have not been completely deactivated and pose many risks.
While operational vulnerabilities are the main cause of $1.83 billion in losses across both DeFi and CeFi platforms, a new threat is rapidly emerging: artificial intelligence (AI). While deep integration of AI and large language models (LLMs) into the Web3 ecosystem brings positive innovations, it also significantly expands the attack surface.
The report notes that AI-related attack incidents have increased by 1,025% compared to 2023, with 98.9% originating from improperly secured application programming interfaces (APIs).
Currently, about 34% of Web3 projects have deployed AI agents in production environments, making them attractive targets for hackers. This issue becomes more urgent as traditional cybersecurity standards like ISO/IEC 27001 and NIST were not designed to effectively respond to AI-specific risks, such as model hallucination or prompt injection attacks.
Hacken emphasizes the need to quickly update these security standards to accurately reflect the emerging risks from AI that are increasingly impacting the safety of the entire Web3 ecosystem.





