Hash functions generate unique, fixed-length codes for data, ensuring security, integrity, and efficiency in blockchain systems.
In blockchain, hash functions link blocks, verify transactions, and secure wallets using irreversible cryptographic techniques.
Mining uses hash functions to solve puzzles, protecting blockchain networks through high computational costs.

On the grand stage of the digital world, blockchain acts like a transparent, tamper-proof “super ledger,” powering decentralized systems like Bitcoin and Ethereum.
Behind the scenes, hash functions work like invisible sorcerers, weaving a safety net with mathematics to ensure data integrity, trustworthy transactions, and system stability. But how exactly do hash functions cast their magic in blockchain? Let’s dive into this backstage story through vivid examples!
HASH FUNCTIONS: A “UNIQUE FINGERPRINT” FOR DATA
Imagine you have an important email that says “I love eating apples.” You throw this email into a “hash machine,” and it instantly spits out a fixed-length string, such as “a1b2c3d4.” This string is the hash value—like a unique fingerprint for the email. The magic of a hash function lies in several characteristics: first, the same email will always generate the same “a1b2c3d4”; second, it’s nearly impossible for anyone to guess the original message from “a1b2c3d4”; third, if you change the email to “I love eating bananas,” the hash value will change completely, like to “x9y8z7w6”;
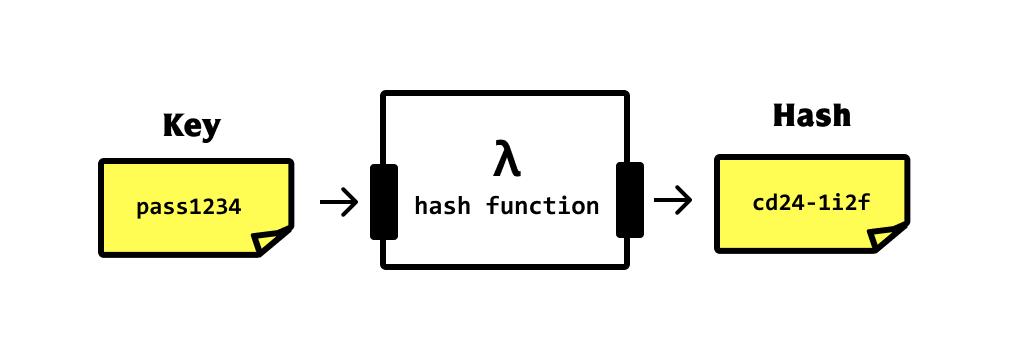
lastly, the chance of two different messages generating the same hash is nearly zero. These traits make hash functions the “security guards” of blockchain. For example, Bitcoin uses the SHA-256 algorithm to turn any data into a 256-bit “fingerprint”—fast and secure.
BLOCK CONNECTION: CHAINED TO PREVENT TAMPERING
Blockchain is like a ledger organized in chronological pages, where each “page” is a block that records transaction data. How do hash functions ensure that this ledger can’t be tampered with? Imagine a Bitcoin block recording a transaction where Xiaoming sends 10 bitcoins to Xiaohong. This block generates a hash using SHA-256, say “1234abcd,” which not only includes the transaction data but also the hash of the previous block, say “5678efgh.” This way, blocks are “chained” using hash values.
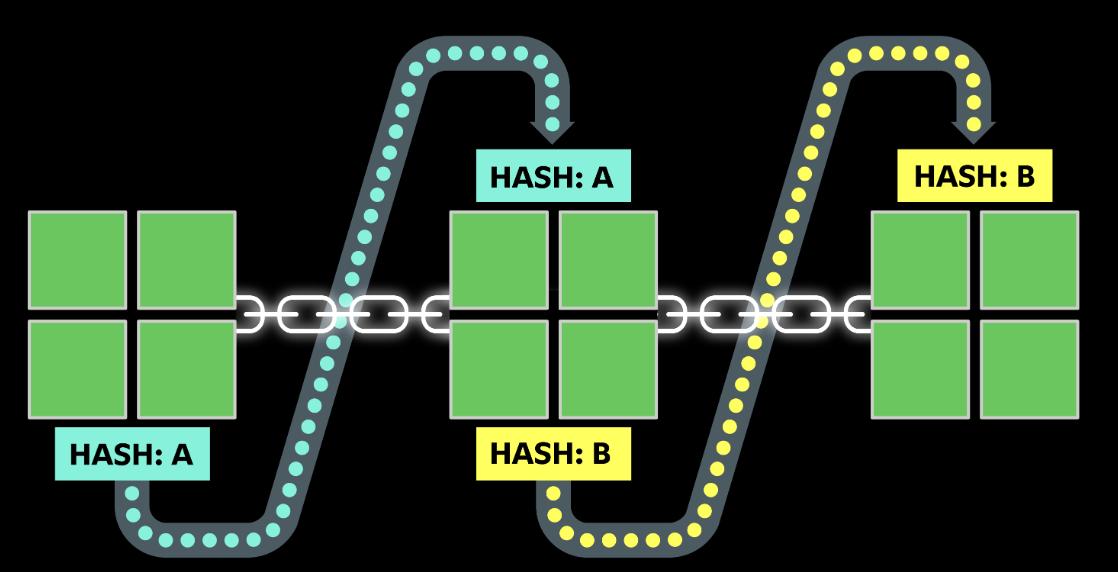
If someone tries to secretly change the transaction from 10 to 100 bitcoins, the block’s hash value will instantly become something completely different, like “9xyz7890,” breaking the entire chain because all following blocks rely on previous hashes.
Tampering with one block means recalculating the entire chain’s hashes—a task that would require massive computational power and is practically impossible. This linked mechanism makes Bitcoin’s transaction history rock-solid.
MINING COMPETITION: A “GUESSING GAME” OF INTELLIGENCE
Bitcoin “mining” may sound like digging for gold in the digital realm, but it’s actually a “brain game” hosted by hash functions. Suppose miner Xiao Li is trying to mine a new block with multiple transactions. He must find a special number (Nonce) so that the block’s hash meets a specific condition—like starting with four zeros (e.g., “0000fghi”).
Xiao Li’s computer keeps trying different numbers—1, 2, 3…—and calculates the hash each time using SHA-256 until it finds the right one (e.g., Nonce = 12345) that meets the requirement. It’s like finding a winning lottery number, consuming tons of time and electricity.

This high cost ensures the blockchain’s security: an attacker trying to alter history would need more computing power than the entire network combined—an immensely expensive task.
TRANSACTION VERIFICATION: A “DIGITAL ID” FOR EVERY TRADE
Each blockchain transaction has an “ID card”—a transaction ID generated by a hash function. For example, Xiaohong buys a digital cat NFT (non-fungible token) with Ethereum. This transaction includes her wallet address, the seller’s address, and the amount of Ether paid.
The transaction data is hashed using Keccak-256 (Ethereum’s algorithm) to generate a transaction ID, such as “7b8c9d.” This ID guarantees the transaction’s uniqueness and integrity. If someone tries to change Xiaohong’s payment from 1 ETH to 10 ETH, the transaction ID immediately changes, say to “2a3b4c,” exposing the fraud. This digital ID system ensures every transaction on the blockchain is quickly verifiable—so NFT buyers like Xiaohong can trade with confidence.
MERKLE TREE: ORGANIZING THOUSANDS OF TRANSACTIONS EFFICIENTLY
A single block may contain thousands of transactions. For instance, a Bitcoin block may record transfers among hundreds of users like Xiaoming and Xiaohong. How can such a volume be efficiently verified? The hash function lends a hand through the “Merkle Tree.” Imagine an upside-down tree: each transaction (like Xiaoming’s 10-BTC transfer) is hashed using SHA-256 to create “h1,” and the transaction next to it (like Xiaohong’s 5-BTC transfer) is hashed into “h2.” These two hashes are then combined and hashed again to create a new hash “h12.”
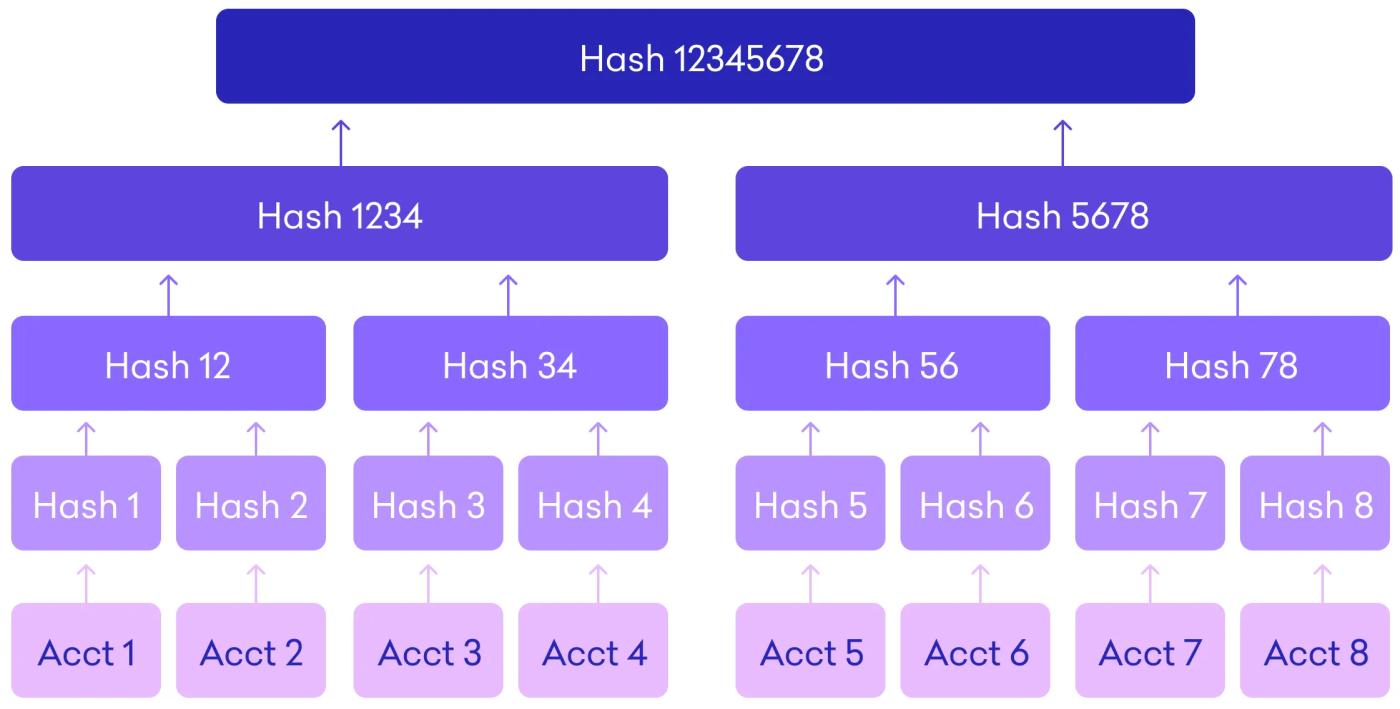
This process continues layer by layer until it produces a compact “Merkle Root,” such as “m123.” Despite its small size, this root hash represents all the transactions in the block. By checking the Merkle Root alone, one can verify that no transactions have been tampered with. In 2021, Bitcoin generated a new block every 10 minutes, and Merkle Trees enabled lightning-fast verification, saving tons of storage.
ADDRESS GENERATION: PROTECTING YOUR DIGITAL WALLET
Your blockchain wallet address—say, a Bitcoin address like “1A2B3C”—where does it come from? It’s actually derived from your public key using hash functions. Suppose Xiaogang creates a Bitcoin wallet, and his public key is a very long string of numbers. This key is processed through SHA-256 and then RIPEMD-160 to compress it into a short, sleek address. The process is like shrinking a long article into a headline—others can send money to this address, but can’t reverse-engineer his private key. This one-way property keeps Xiaogang’s funds secure.
CONCLUSION
From chaining blocks to managing mining, verifying transactions to protecting privacy, hash functions are the “digital sorcerers” of blockchain—guarding this decentralized world with strings of “fingerprints.” Whether it’s Xiaoming’s Bitcoin transfer, Xiaohong’s NFT purchase, or Xiaogang’s wallet address, hash functions work silently behind the scenes. So next time you hear about the wonders of blockchain, think about those tiny hash values—they’re the mathematical force holding up a transparent and secure digital future!
〈What Is a Hash Function? The Core Algorithm Behind Blockchain〉這篇文章最早發佈於《CoinRank》。