Next, replace the PRIVATE_KEY in the .env file with the newly generated test private key.

Then, launch the malicious code and observe the response from the server-side interface.

We can see that the test server successfully received the JSON data sent by the malicious project, which includes the PRIVATE_KEY information.

Indicators of Compromise (IoCs)
IPs:
103.35.189.28
Domains:
storebackend-qpq3.onrender.com
SHA256:
07f0364171627729788797bb37e0170a06a787a479666abf8c80736722bb79e8 - pumpfun-pumpswap-sniper-copy-trading-bot-master.zip
ace4b1fc4290d6ffd7da0fa943625b3a852190f0aa8d44b93623423299809e48 - pumpfun-pumpswap-sniper-copy-trading-bot-master/src/common/config.rs
Malicious Repository:
https://github.com/audiofilter/pumpfun-pumpswap-sniper-copy-trading-bot
Similar Implementation Methods:
https://github.com/BitFancy/Solana-MEV-Bot-Optimized
https://github.com/0xTan1319/solana-copytrading-bot-rust
https://github.com/blacklabelecom/SAB-4
https://github.com/FaceOFWood/SniperBot-Solana-PumpSwap
https://github.com/Alemoore/Solana-MEV-Bot-Optimized
https://github.com/TopTrenDev/Raypump-Executioner-Bot
https://github.com/deniyuda348/Solana-Arbitrage-Bot-Flash-Loan
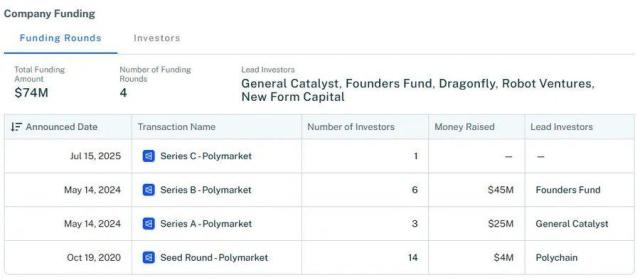
Summary
In this attack method, the attacker disguises themselves as a legitimate open-source project, inducing users to download and execute the malicious code. The project reads sensitive information from the local .env file and transmits the stolen private key to a server controlled by the attacker. Such attacks often combine social engineering techniques, and users can easily fall victim with just a slight oversight.
We recommend that developers and users remain highly vigilant about GitHub projects of unknown origin, especially those involving wallet or private key operations. If it is necessary to run or debug, it is advised to do so in an isolated environment without sensitive data, avoiding the execution of malicious programs and commands from unknown sources.
For more security knowledge, refer to the "Blockchain Dark Forest Self-Rescue Handbook" by SlowMist:
https://github.com/slowmist/Blockchain-dark-forest-selfguard-handbook/blob/main/README_CN.md
Disclaimer: As a blockchain information platform, the articles published on this site represent only the personal views of the authors and guests, and are not related to the position of Web3Caff. The information in the articles is for reference only and does not constitute any investment advice or offer. Please comply with the relevant laws and regulations of your country or region.
Welcome to join the Web3Caff official community: X(Twitter) Account丨Web3Caff Research X(Twitter) Account丨WeChat Reader Group丨WeChat Official Account