GMX suffered an attack, where the attacker exploited a reentrancy vulnerability in the project's contract, profiting approximately $42 million. The Beosin security team conducted a vulnerability analysis and fund tracking of this attack event, and shared the following results:
Detailed Attack Steps
The attacker first used the margin refund mechanism in the executeDecreaseOrder function of the OrderBook contract to launch a reentrancy attack to bypass the project's Timelock contract leverage switch:
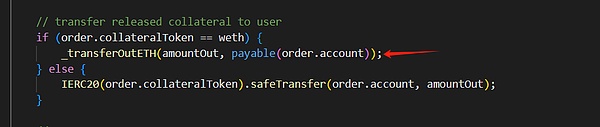
Then, the attack borrowed USDC through a flash loan for staking and minting GLP, while increasing a BTC short position with USDC as margin, causing the GLPmanager contract's AUM value to be artificially high, which affects the GLP price calculation.
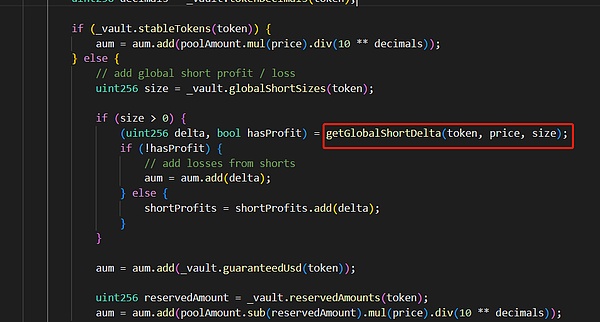
Finally, the attacker redeemed GLP at an abnormal price for profit and specified the exchange to other tokens.
Vulnerability Analysis
Through the above attack process, we can see that the vulnerability exploitation reasons for the entire event are as follows:
- Lack of reentrancy protection, allowing internal state modification during redemption.
- Complex redemption logic with insufficient security verification.
Although GMX underwent multiple security audits, this reentrancy vulnerability was still overlooked. If the redemption logic had been subjected to stricter checks and considered potential reentrancy vulnerabilities, such security incidents might have been avoided.
Stolen Funds Tracking
Beosin Trace's tracking of stolen funds revealed: The attacker's address 0x7d3bd50336f64b7a473c51f54e7f0bd6771cc355 profited approximately $42 million, then converted stablecoins and Altcoins to ETH and USDC through multiple cross-chain protocols, transferring stolen assets to the Ethereum network. Currently, approximately $32 million worth of ETH from the stolen assets is stored in the following 4 Ethereum network addresses:
- 0xe9ad5a0f2697a3cf75ffa7328bda93dbaef7f7e7
- 0x69c965e164fa60e37a851aa5cd82b13ae39c1d95
- 0xa33fcbe3b84fb8393690d1e994b6a6adc256d8a3
- 0x639cd2fc24ec06be64aaf94eb89392bea98a6605
Approximately $10 million in assets are stored in the address 0xdf3340a436c27655ba62f8281565c9925c3a5221 on the Arbitrum network. Beosin Trace has added the hacker-related addresses to its blacklist and will continue to track them.
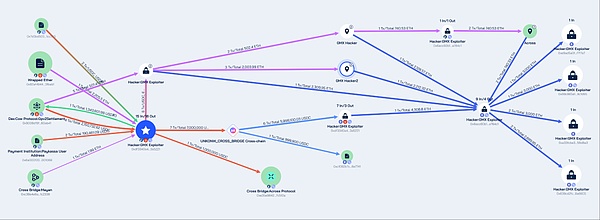
According to Beosin Trace analysis, all stolen funds remain in multiple addresses of the attacker
Conclusion
The core of this attack was the reentrancy vulnerability in the GMX contract, allowing the attacker to redeem large amounts of assets for profit through artificially inflated AUM values. For complex DeFi protocols like GMX, multi-dimensional and multi-layered security audits are needed, with thorough testing and review of contract code. Previously, the Beosin security team has completed security audits for multiple DeFi protocols (such as Surf Protocol, SyncSwap, LeverFi, Owlto Finance), focusing on discovering contract logic defects and potentially overlooked extreme scenarios to ensure comprehensive DeFi protocol detection.